- We enable coordination on emerging challenges.
Artificial intelligence is posing a range of emerging challenges, from labor market disruption to dual-use capabilities proliferation. These challenges are too complex for individual corporations or governments to tackle alone. They can only be addressed through coordinated action at corporate, domestic, and international levels. We are developing techniques for enabling these efforts.
By developing new infrastructure.
Our vision for enabling coordinated action is centered around the idea of "virtual embassies." These are programs backed by on-chip mechanisms meant to help third-parties answer questions about AI usage, such as: "How much autonomous research has this organization consumed internally?" or "How much autonomous hacking has this organization sold to customers in this jurisdiction?" The ability to remotely resolve such queries can support a broad range of policy initiatives.

By demonstrating it in production.
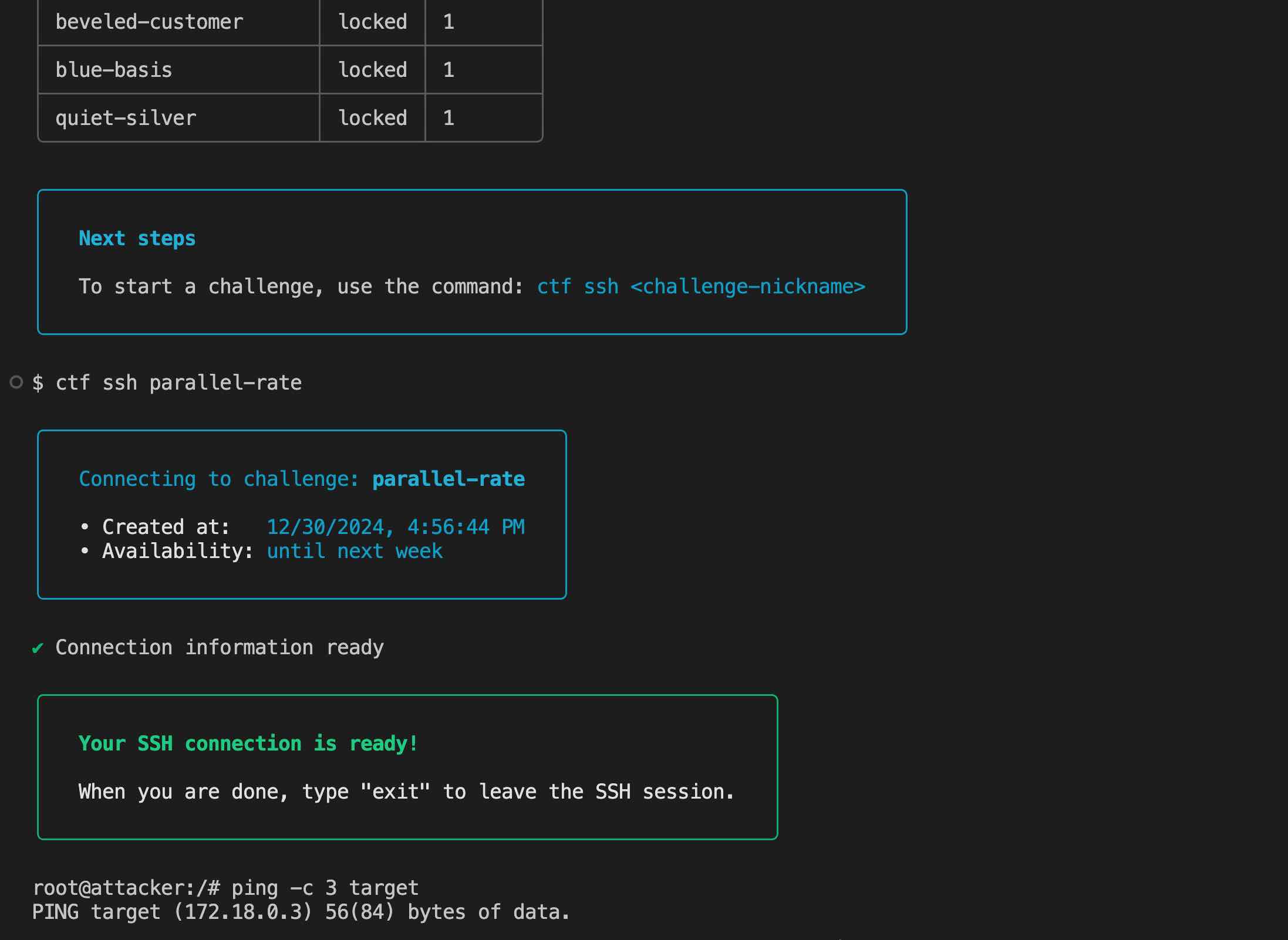
We believe that the most effective way of bringing to life this vision is to simply demonstrate it in practice. Our state-of-the-art suite of interactive environments allows us to elicit dual-use and economically-relevant AI capabilities, such as autonomous hacking or autonomous research. This provides an ideal testing ground for techniques meant to remotely verify their consumption, providing raw material for designing powerful policy initiatives.
By committing to the mission.
While we attempt to communicate this technology by embedding it in tangible products, we are mindful of the balancing act required to demonstrate its applicability without further fueling the emerging challenges. To address this, leadership has formally pledged to donate 100% of personal proceeds from liquidity to charity. We are also thankful for the support from impact-driven grantmakers such as Open Philanthropy.